| KERNEL DETOURS (with source code) |
INTRODUCTION
The Detours library is an interesting project from the people at Microsoft Research. The concept and implementation of the core library (the one that I am used to use; the other features of the library -remote process code injection, dll injection etc- are techniques I usually accomplish with proprietary solutions) is really simple: if you need to "detour" an API entry point (i.e. to redirect the processor execution to an implementation of yours and then, eventually, to restore the execution to the original implementation) then the Detours library disassembles that entry point at assembler level, determines whether that code can be copied elsewhere in virtual memory and then calculates a minimum number of bytes that need to be trasferred in order to move the first instructions of that entry point in a special structure that the authors of the library have named "trampoline". So, when the processor executes the detoured API, it will find a JMP instruction instead of the first original instructions belonging to the function in question. The so injected JMP instruction points to an implementation provided by the consumer of the Detours library: in this function, the programmer can set up infinite types of interception and hook logics. When the hook has finished its work, then it can return to the very original caller of the detoured API (thus bypassing completely the original detoured function) or can call the trampoline, which in turn executes the original instructions of the detoured function (the ones that were replaced by the JMP code) and finally executes a second JUMP that restores the processor instruction pointer to a proper position inside the original function. This is a representation of what happens at assembler level in a nice hand-made Paint Shop Pro representation:
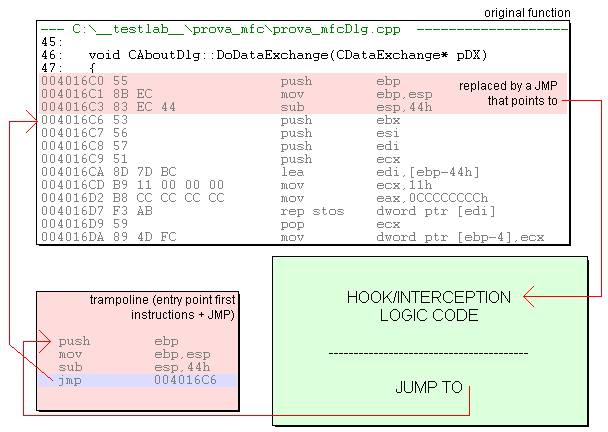
The idea behind the Detours library is noway new to hook code programmers: there is a plenty of techniques for achieving function code interception (I will remember here just a few of these: (1) import table patching, (2) export table patching, (3) a very nice trick by Matt Pietrek -IIRC- that involves playing around with breakpoint exceptions and the trace bit in the flags etc.). In my opinion, the solution implemented in the Detours library is just the more clear, robust (it is inherently SMP-safe) and simply to code.
You can achieve the same final effect of the Detours library by using one of the many free x86 disassemblers on the web and then by reimplementing the entry point byte move logic that I have explained earlier.
KERNEL DETOURS
One of the main limitations of the original Detours library (besides the non-commercial restrictions) is the lack of support for kernel mode detours: the original library makes hard-coded calls to user mode APIs such as VirtualProtect and FlushInstructionCache that, obviously, are not exported to kernel mode drivers. Furthermore the library code that patches the application target code is integrated into the Detours disassembler implementation: this is NOT a good thing when you are patching the entry point of a keyboard ISR or of a crucial high-concurrency kernel function. In these cases it may be useful to run the disassembler and the patching code separately: applying the JMP patch may require, for example, some sort of intra-processor syncronization method (such as disabling the interrupts or raising the IRQL to HIGH_LEVEL) or of inter-processor synchronization (such as an hand-made IPI interrupt or more realistically a more practical equivalent such as an high-importance targeted DPC...).
So I have taken the original C++ source codes of the Detours library and I have converted them in a single C file ready to be linked against a kernel mode driver project. In any case, it should be clear that doing this sort of things in kernel space can have extremely disastrous effects when you don't know exactly what you are doing: besides the very important synchronization issue, there are other problems to take into account such as the write-access patching of a kernel-mode real-only (code) section, for example. For the articles published on this web-site I have used more than once the kernel-enabled version of the Detours library: for examples of real-world uses of the modified version of the library (and for a more in-depth explanation of the related problems), check out the following articles:
DOWNLOAD
Download the .C source file of the modified Kernel Detours library from here. (66KB)
|
|
|
|
|

|
|
|

|
|
Photos |
Various images from italian conferences and events (keep the mouse
on a thumbnail for a short description):
|
 |
 |
 |
 |
|
|
|

|
| Site
login |
| NOTE: Actually the login feature is used only for
administrative and content management purposes.
|
|
|
|
|
|
|
|
Everything here (code, binaries, text, graphics, design, html) is © 2010 Vito
Plantamura and VPC Technologies SRL (VATID: IT06203700965).
If you download something (compilable or not) from the site, you should read
the license policy file.
If you want to contact me via email, write at this
address. |
|
|